All
Microsoft supports EU Signature standard in Office 2010
2010-Apr-30 09:51
Microsoft has decided to support the EU digital signature format XAdES in Office 2010.
Read more about this at: http://blogs.technet.com/office2010/archive/2009/12/08/digital-signitures-in-office-2010.aspx
This format builds on the XML Digital signature standard from W3C which is the globally accepted standard for XML signatures.
Read More...
Read more about this at: http://blogs.technet.com/office2010/archive/2009/12/08/digital-signitures-in-office-2010.aspx
This format builds on the XML Digital signature standard from W3C which is the globally accepted standard for XML signatures.
Read More...
Internationalization - A growing pain for Internet protocol design
2009-Nov-16 06:34
International characters are becoming a growing pain for Internet protocol design.
Many protocols just deal with 7-bit ASCII on the basic protocol level while there is an increasing demand for information expression in local languages at the application layer. Various protocols like Internet mail and DNS has addressed this issue by defining conventions to carry international characters over 7-bit ASCII. The problem is rather straightforward as long as the task is limited to presentation of data in a local language context, but grows to a very hard problem when the task is expanded to comparison of canonicalized strings from different sources. The problem is even harder if consistency between visual matching and matching of encoded character strings is required.
The technical plenary at the 76th IETF in Hiroshima (November 8-13 2009) recently focused in on this particular problem. Read More...
Many protocols just deal with 7-bit ASCII on the basic protocol level while there is an increasing demand for information expression in local languages at the application layer. Various protocols like Internet mail and DNS has addressed this issue by defining conventions to carry international characters over 7-bit ASCII. The problem is rather straightforward as long as the task is limited to presentation of data in a local language context, but grows to a very hard problem when the task is expanded to comparison of canonicalized strings from different sources. The problem is even harder if consistency between visual matching and matching of encoded character strings is required.
The technical plenary at the 76th IETF in Hiroshima (November 8-13 2009) recently focused in on this particular problem. Read More...
TLS Cached Info update
2009-Nov-12 03:19
I’m currently writing a new standard for TLS which will allow the client to cache big portions of static data exchanged during TLS handshake negotiations and allow the server to omit resending this data on consecutive handshakes, such as in consecutive re-negotiations.
My slides for the TLS meeting today at the Hiroshima IETF, showing the basic approach. is available here: Cached Info (PDF).
Read More...
My slides for the TLS meeting today at the Hiroshima IETF, showing the basic approach. is available here: Cached Info (PDF).
Read More...
Null Prefix attack against TLS Server Certificates
2009-Nov-12 02:49
A new embarrassing attack was recently discovered and exploited on Server Certificates and their validation in many current browser environments.
The discovery is that current deployment of domain name matching between the domain expressed in the certificate and the domain protected by the certificate use string matching which treat character 00 (\0) as end of string.
Read More...
The discovery is that current deployment of domain name matching between the domain expressed in the certificate and the domain protected by the certificate use string matching which treat character 00 (\0) as end of string.
Read More...
New attack against TLS
2009-Nov-12 02:32
The TLS workgroup in the IETF (Internet Engineering Task Force) is currently heavily engaged in finding a quick solution to the just recently discovered and published attack against TLS using TLS renegotiaion. Read More...
The problem of keeping a blog as expert consultant
2009-Sep-15 11:08
I have realized that there are may ways to keep a blog.
One goal is to write something everyday regardless of whether you have anything to say or not. That is not the path i I like to choose.
So I like to turn here and write about things that;
Unfortunately the third is quite a limiting factor. Sometimes the most interesting things at hand I would like to write about is something that my customers do not wish to have published on my blog. And that is something I have to respect.
Read More...
One goal is to write something everyday regardless of whether you have anything to say or not. That is not the path i I like to choose.
So I like to turn here and write about things that;
- i find interesting,
- i think someone else might have interest in, and;
- does not violate reasonable confidentiality agreements with my customers.
Unfortunately the third is quite a limiting factor. Sometimes the most interesting things at hand I would like to write about is something that my customers do not wish to have published on my blog. And that is something I have to respect.
Read More...
Man in the middle attack against Extended Validation protected Web sites
2009-Jul-15 23:27
Two security researchers are presenting a man in the middle attack against Extended Validation (EV) protected websites through what they term “SSL Rebinding”.
The basic problem is that modern websites combines information from many sources simultaneously when providing services to users. The problem a browser faces is to decide when it is valid to show the Extended Validation protection level by the “green bar”, or similar UI distinction, when only part of the visible content is provided through an EV certificate protected TLS(SSL) session.
Some sites, such as PayPal provide part of the content through EV protected TLS while other parts are just protected using a Domain Validation (DV) certificate, but web browsers will still regard the whole session as EV protected.
The researchers claim to have found an attack that effectively exploits this and will present their result at the upcoming Black Hat conference.
Read More...
The basic problem is that modern websites combines information from many sources simultaneously when providing services to users. The problem a browser faces is to decide when it is valid to show the Extended Validation protection level by the “green bar”, or similar UI distinction, when only part of the visible content is provided through an EV certificate protected TLS(SSL) session.
Some sites, such as PayPal provide part of the content through EV protected TLS while other parts are just protected using a Domain Validation (DV) certificate, but web browsers will still regard the whole session as EV protected.
The researchers claim to have found an attack that effectively exploits this and will present their result at the upcoming Black Hat conference.
Read More...
Minimum requiriments for electronic signatures in Europe may disqualify perfectly valid signatures
2009-Jul-03 03:08
Various activities in Europe tries, in light of the Services directive, to establish minimum requirements for Advanced Electronic Signatures in Europe.
The background of the electronic signature directive and the electronic signature standards in Europe makes this a hard and potentially dangerous task where we run a risk of disqualifying most signature capable products for no obvious gain.
Read More...
The background of the electronic signature directive and the electronic signature standards in Europe makes this a hard and potentially dangerous task where we run a risk of disqualifying most signature capable products for no obvious gain.
Read More...
EU Identity project turns its back on Information Card
2009-Jun-29 23:46
The EU Commission funded project STORK announced during its second Industry Group Meeting, that they have decided on SAML 2.0 as protocol for its technical architecture.
The STORK project is the primary pilot project assigned by the EU commission to test cross border electronic identification between citizens and electronic services across Europe.
The first Industry Group Meeting resulted in feedback suggesting that the proposed architecture have potential vulnerabilities with respect to man in the middle attacks.
The combination of the solution to this problem and the selection of SAML 2.0 as the protocol of choice effectively prevents the use of the Information Card technology developed by the Industry during the past five years. The reason for this is that the Information Card model, which also use SAML assertions, uses WS-Trust as its primary exchange protocol and not pure SAML.
Read More...
The STORK project is the primary pilot project assigned by the EU commission to test cross border electronic identification between citizens and electronic services across Europe.
The first Industry Group Meeting resulted in feedback suggesting that the proposed architecture have potential vulnerabilities with respect to man in the middle attacks.
The combination of the solution to this problem and the selection of SAML 2.0 as the protocol of choice effectively prevents the use of the Information Card technology developed by the Industry during the past five years. The reason for this is that the Information Card model, which also use SAML assertions, uses WS-Trust as its primary exchange protocol and not pure SAML.
Read More...
New Internet Draft Nroff editor
2009-Jun-17 04:32
I have written and made available an Internet Draft editor for writing drafts in Nroff format.
The Nroff format was the dominant way to format draft and RFC documents in the past and many draft writers still use the Nroff format with some command line compiler.
As I failed to find any decent application with which I could edit an nroff file and see the result in one application, I decided to write my own in
NroffEdit as a Java application distributed as jar file and is prepared for Mac and Windows.
For more information see http://aaa-sec.com/nroffedit/index.html
I appreciate any comments, feedback suggestions or bug reports.
Read More...
The Nroff format was the dominant way to format draft and RFC documents in the past and many draft writers still use the Nroff format with some command line compiler.
As I failed to find any decent application with which I could edit an nroff file and see the result in one application, I decided to write my own in
NroffEdit as a Java application distributed as jar file and is prepared for Mac and Windows.
For more information see http://aaa-sec.com/nroffedit/index.html
I appreciate any comments, feedback suggestions or bug reports.
Read More...
IETF agrees to develop Visual eID standard
2009-May-14 14:35
The PKIX group of the Internet Engineering Task Force has decided to adopt the work item to develop a standard for visual representation of e-identification certificates.
The PKIX group accepted the draft proposed by the Visual eID project as starting point for the standards work.
The current PKIX draft can be found here. Read More...
The PKIX group accepted the draft proposed by the Visual eID project as starting point for the standards work.
The current PKIX draft can be found here. Read More...
Support the Visual eID work in PKIX
2009-May-04 11:11
The current status of the Visual eID standardisation process is for IETF to accept this work as part of its agenda.
The Visual eID standard has been proposed to be added to the PKIX WG agenda and its acceptance is currently up for open discussion.
The draft standard under discussion is found at: http://tools.ietf.org/html/draft-santesson-pkix-certimage-00
You can influence the decision in the IETF/PKIX and take part in the development discussion by posting your view at the PKIX mailing list. This list is open for anyone who wishes to attend.
To subscribe to the PKIX mailing list send an e-mail to: ietf-pkix-request@imc.org
In the body of the e-mail enter “subscribe”
To support this work being adopted as a PKIX work item, send a mail to the PKIX mailing list: ietf-pkix@imc.org
The following message can be used:
“I support adoption of draft-santesson-pkix-certimage-00 as PKIX work item”
Click here to generate a ready composed e-mail.
Read More...
The Visual eID standard has been proposed to be added to the PKIX WG agenda and its acceptance is currently up for open discussion.
The draft standard under discussion is found at: http://tools.ietf.org/html/draft-santesson-pkix-certimage-00
You can influence the decision in the IETF/PKIX and take part in the development discussion by posting your view at the PKIX mailing list. This list is open for anyone who wishes to attend.
To subscribe to the PKIX mailing list send an e-mail to: ietf-pkix-request@imc.org
In the body of the e-mail enter “subscribe”
To support this work being adopted as a PKIX work item, send a mail to the PKIX mailing list: ietf-pkix@imc.org
The following message can be used:
“I support adoption of draft-santesson-pkix-certimage-00 as PKIX work item”
Click here to generate a ready composed e-mail.
Read More...
SHA-1 taking a significant hit
2009-May-01 01:58
SHA-1 has taken a significant hit.
Recent presentation at the EuroCrypt rump session suggest that the problem to find SHA-1 collision is reduced to 2^52.
This is a significant reduction from the previously known best path with complexity 2^63.
For details, see:
http://eurocrypt2009rump.cr.yp.to/837a0a8086fa6ca714249409ddfae43d.pdf
Read More...
Recent presentation at the EuroCrypt rump session suggest that the problem to find SHA-1 collision is reduced to 2^52.
This is a significant reduction from the previously known best path with complexity 2^63.
For details, see:
http://eurocrypt2009rump.cr.yp.to/837a0a8086fa6ca714249409ddfae43d.pdf
Read More...
FIrst visual eID draft posted
2009-Apr-22 12:20
The first IETF draft is posted:
draft-santesson-pkix-certimage-00
The first draft is a result from an initial design process within the editorial team as well as discussions with partners and members of the CA Browser Forum.
This draft will initiate discussion in the PKIX WG whether to accept this as an adopted work item.
Read More...
draft-santesson-pkix-certimage-00
The first draft is a result from an initial design process within the editorial team as well as discussions with partners and members of the CA Browser Forum.
This draft will initiate discussion in the PKIX WG whether to accept this as an adopted work item.
Read More...
Scalable Image Formats
2009-Apr-20 14:14
In the discussions concerning a visual image of an identity certificate, the image format of choice is a hot topic.
The issuer of the certificate knows what the image should look like but don’t know the type, size and resolution of the screen where it will be displayed. Therefore, what we need is a scalable image format that can render text and graphical elements.
Choosing one image format has however turned out to be a bit problematic.
Read More...
The issuer of the certificate knows what the image should look like but don’t know the type, size and resolution of the screen where it will be displayed. Therefore, what we need is a scalable image format that can render text and graphical elements.
Choosing one image format has however turned out to be a bit problematic.
Read More...
Visual eID Problem Statement posted
2009-Apr-18 03:32
Based on input and discussions around the Visual eID project, I have written a problem statement which will be a living document for the project.
This document attempts to capture on a few pages, the basic problems and scenarios as well as the main reasons why this work is needed.
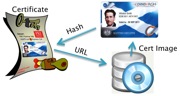
This living document is available here.
Comments and inputs are highly appreciated. Read More...
This document attempts to capture on a few pages, the basic problems and scenarios as well as the main reasons why this work is needed.

This living document is available here.
Comments and inputs are highly appreciated. Read More...
Visual eID submitted to ISSE 2009
2009-Apr-03 01:55
The visual eID standards effort has been submitted to the Information Security Solutions Europe conference in Hague, October 2009.
The submitted abstract below provide some basic rationales and orientation:
Abstract:
Since the EU directive on electronic signatures was published in 1999, national certification authorities have issued millions of certificates and qualified certificate. But have you actually seen one?
It is a paradox, considering that development of standards for electronic identification using Public Key Cryptography has been going on for a bit over 20 years by now, that we still have no generic solution or standard for how to display a certificate based identity to a human being.
Read More...
The submitted abstract below provide some basic rationales and orientation:
Abstract:
Since the EU directive on electronic signatures was published in 1999, national certification authorities have issued millions of certificates and qualified certificate. But have you actually seen one?
It is a paradox, considering that development of standards for electronic identification using Public Key Cryptography has been going on for a bit over 20 years by now, that we still have no generic solution or standard for how to display a certificate based identity to a human being.
Read More...
Strong editorial team for visual eID standard
2009-Mar-31 08:14
During IETF last week in San Francisco we managed to form a really strong editorial team for the new visual eID standard.
This standard will make it possible to bind a visual representation of a certificate to its signature. More information about this project is available on my Visual eID information page.
The editorial team:
Stefan Santesson, 3xA Security is lead editor as initiator and driver of this standards effort.
Russ Housley, Vigil Security. Russ is chairman of the Internet Engineering Task Force and was also co-editor of the original standard RFC 3709 on which this standards effort is based.
Siddharth Bajaj, VeriSign. VeriSign as the world leading provider of public certificates for web servers has been actively promoting a better UI experience for certificate based identification and authorisation. Siddharth has been actively involved with these efforts for almost a decade.
Leonard Rosenthol, Adobe. This standards effort was made possible much thanks to the standardisation of PDF in 2008. Leonard is the standards architect behind the development of an ETSI standard for PDF based Advanced Electronic Signatures (PAdES).
The work to write this standard will start immediately and a first draft will be published soon, no later than end of April. Read More...
This standard will make it possible to bind a visual representation of a certificate to its signature. More information about this project is available on my Visual eID information page.
The editorial team:
Stefan Santesson, 3xA Security is lead editor as initiator and driver of this standards effort.
Russ Housley, Vigil Security. Russ is chairman of the Internet Engineering Task Force and was also co-editor of the original standard RFC 3709 on which this standards effort is based.
Siddharth Bajaj, VeriSign. VeriSign as the world leading provider of public certificates for web servers has been actively promoting a better UI experience for certificate based identification and authorisation. Siddharth has been actively involved with these efforts for almost a decade.
Leonard Rosenthol, Adobe. This standards effort was made possible much thanks to the standardisation of PDF in 2008. Leonard is the standards architect behind the development of an ETSI standard for PDF based Advanced Electronic Signatures (PAdES).
The work to write this standard will start immediately and a first draft will be published soon, no later than end of April. Read More...
Cert Cache adopted as TLS standards work
2009-Mar-26 19:26
Today (March 26) at the IETF 74 conference, the TLS working group decided to adopt the certificate cache work with the intention to develop this to a new TLS standard. The decision was made after my presentation of the certcache proposal at the TLS working group.
The basic idea behind this proposal can be found in this blog article.
The first draft (draft-santesson-tls-certcache-00) is available here
Read More...
The basic idea behind this proposal can be found in this blog article.
The first draft (draft-santesson-tls-certcache-00) is available here
Read More...
PKIX Meeting Minutes and Presentations
2009-Mar-25 18:32
The PKIX group of the Internet Engineering Task Force met this Monday in San Francisco.
I made several presentations at this meeting but my main focus was on presenting the Visual eID Project and in particular the standards efforts that is required to form a complete technical solution.
Meeting minutes and presentations are available from http://tools.ietf.org/wg/pkix/minutes Read More...
I made several presentations at this meeting but my main focus was on presenting the Visual eID Project and in particular the standards efforts that is required to form a complete technical solution.
Meeting minutes and presentations are available from http://tools.ietf.org/wg/pkix/minutes Read More...
Visual eID project presented at PKIX, March 23
2009-Mar-22 02:32
On Monday March 23, I will present the standards mission of the Visual eID project at the PKIX meeting at the IETF 74 in San Francisco.
The presentation is available here
I’m currently looking for partners and sponsors for this project and for this purpose I have created a project information page at http://aaa-sec.com/visualeid/.
The presentation is available here
I’m currently looking for partners and sponsors for this project and for this purpose I have created a project information page at http://aaa-sec.com/visualeid/.
ETSI approves new European PDF signature standard
2009-Mar-19 12:57
The Electronic Signature Initiative group of the European Telecommunication Standards Institute, ETSI ESI, approved PAdES, the European standard for PDF Advanced Electronic Signatures on March 18, 2009.
PAdES, or ETSI standard TS 102 778, is ETSI’s continuation of EU commission funded standardization of Advanced Electronic Signatures in support of the EU Electronic Signature Directive from 1999. PAdES is the third signature standard in the ETSI series covering signatures on PDF documents. Previously published ETSI signature standards have specified signatures on XML documents (XAdES) and signatures using CMS (CAdES) where CMS is the ASN.1 based signature (Cryptographic Message Syntax) developed by IETF as part of the S/MIME standards series for secure e-mail.
Read More...
PAdES, or ETSI standard TS 102 778, is ETSI’s continuation of EU commission funded standardization of Advanced Electronic Signatures in support of the EU Electronic Signature Directive from 1999. PAdES is the third signature standard in the ETSI series covering signatures on PDF documents. Previously published ETSI signature standards have specified signatures on XML documents (XAdES) and signatures using CMS (CAdES) where CMS is the ASN.1 based signature (Cryptographic Message Syntax) developed by IETF as part of the S/MIME standards series for secure e-mail.
Read More...
EU Commission action plan on Electronic Signatures and Electronic Identities
2009-Mar-17 16:13
The EU commission has released an action plan for harmonisation of electronic signatures and electronic identification among European member states.
You can download the action plan here COM (2008) 798final
A presentation on the action plan held at ETSI ESI in Barcelona, March 17 2009 is here Read More...
You can download the action plan here COM (2008) 798final
A presentation on the action plan held at ETSI ESI in Barcelona, March 17 2009 is here Read More...
Updating the IETF Time Stamp standard
2009-Mar-14 01:08
The IETF standard for time stamps is currently being updated - But are the changes really necessary? Read More...
PKI Resource Query Protocol (PRQP) Deployed by Federal Bridge and OpenCA
2009-Mar-11 13:57
A fairly new and unknown protocol, the PKI Resource Query Protocol (PRQP) developed in the IETF PKIX Work Group, is being deployed by the US Federal Bride and OpenCA, reports the editor of the current draft, Massimiliano Pala.
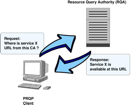
Read More...

Read More...
Defining Hash functions without security properties
2009-Mar-10 03:19
Do we need hash functions with no security properties in order to not confuse their use with cases when security is a requirement. A current discussion in the International standards community is trying to decide whether to standardise hash functions without security properties.
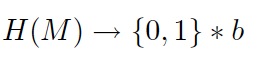 Read More...
Read More...
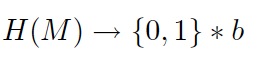 Read More...
Read More...Visual Electronic Identities
2009-Mar-09 14:24
How can we provide applications with standard User Interface tools to display a meaningful representation of an electronic identity (eID)
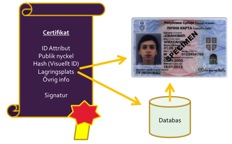 Read More...
Read More...
 Read More...
Read More...Optimising TLS handshake through certificate caching
2009-Mar-09 11:36
A possible but unexplored optimisation of the TLS handshake is to cache server certificates. I’m proposing a new IETF standard that specifies a method to accomplish this. Read More...
All those Passwords
2009-Mar-08 15:19
Passwords are a menace. A discussion I overheard between young students gave me reason to actually feel hopeful.
 Read More...
Read More...
 Read More...
Read More...Welcome to my blog
2009-Mar-04 18:34

In this Blog I provide information and personal thoughts related to Internet security.
I hope you will find some useful thoughts here.
